
It uses our Artificial Intelligence engine with image recognition to verify the correct execution of the most critical steps of a task.
Get visual evidence of the correct execution of tasks and save all data and reports in your ERP, CRM, CMMS management systems.
Train your operators to accelerate their training and guide your beginner technicians to ensure their efficiency and full autonomy.
Features that make your tasks effortless. Process Eye functions allow you to create digital instructions and inspections tailored to your particular processes and needs.
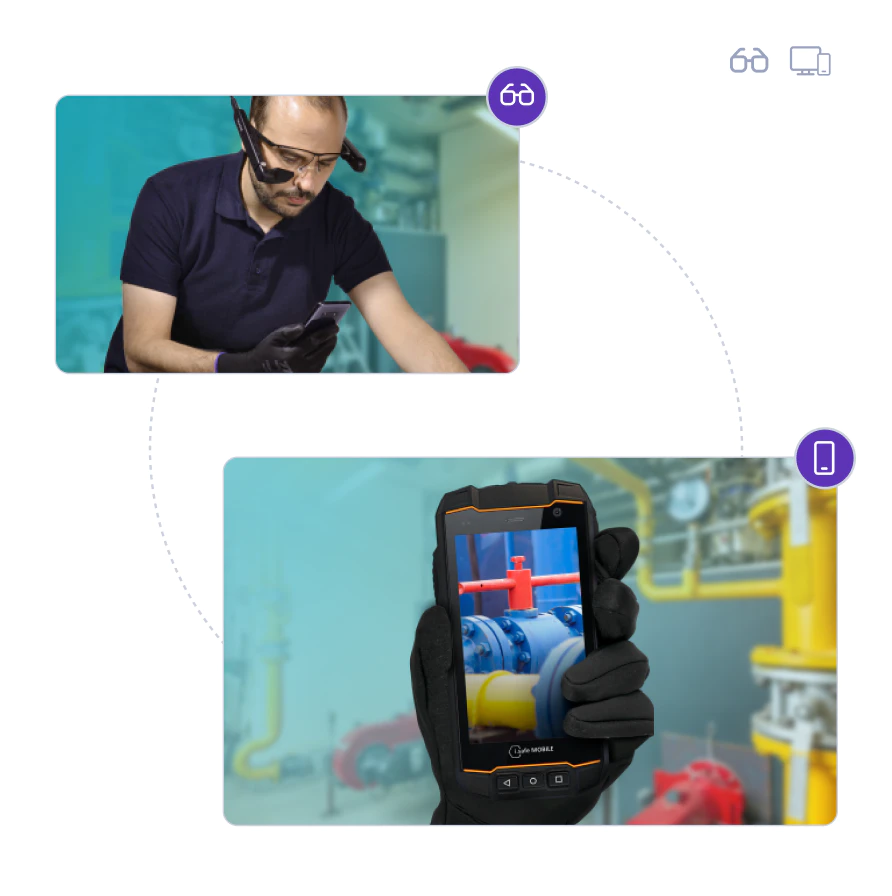
Use it on any device
Use Process eye indifferently on mobiles, computers, tablets and smart glasses.
Automatically monitors performance with Artificial Intelligence
Ensure that critical steps are executed correctly with Machine Learning Image Recognition.
Write without typing: your Voice to Text comments
Take advantage of the speech-to-text transcription function to make comments and annotations that are added to the report.

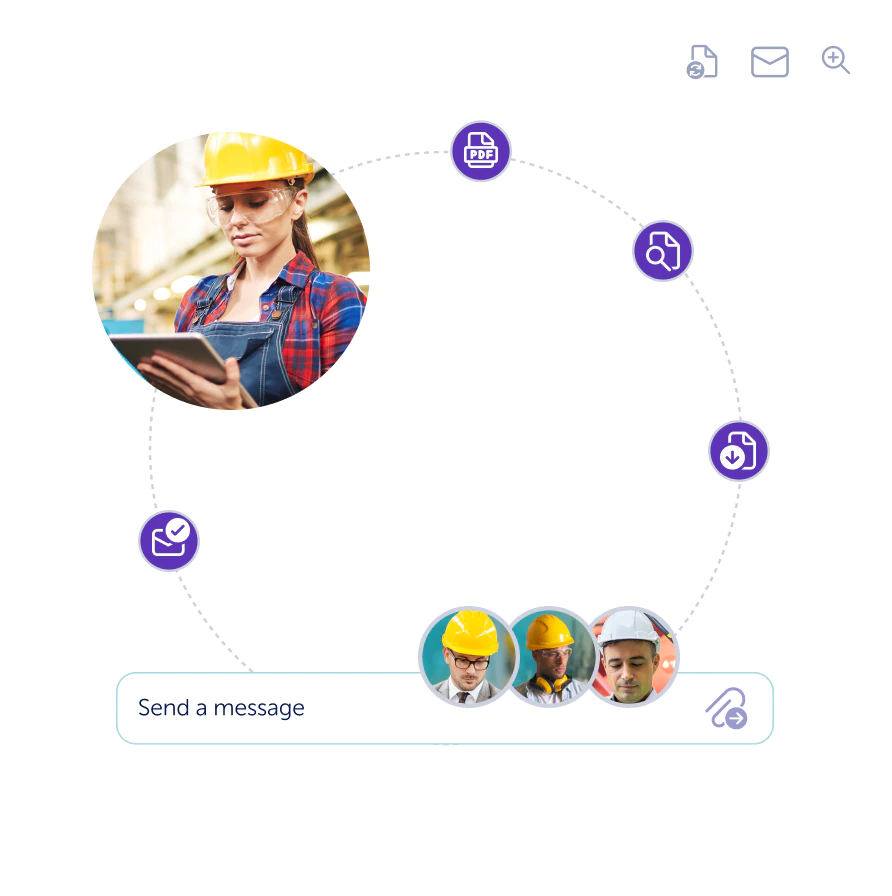


Connect to cloud-based procedures and have all data synchronized and ready to be followed easily with instructions and images.
Track all tasks and steps by taking pictures and create reports automatically.
Encrypted data
We use Transport Layer Security (TLS 1.2) encryption for all transmitted data. Sensible information and other metadata uploaded into our applications is encrypted with AES 256-bit encryption at rest.
Cloud Services
Our servers hosted on AWS, as they are an AICPA SOC 1, SOC 2 type 2 and SOC 3 approved service providers and are ISO 27001, 27017 and 27018 certified. Different options are available to install apps on-premises.
Firewall
In addition to AWS security, antivirus and system firewall, we also use Trend Micro Cloud One - Workload Security (DSaas) as Wideum's Intrusion Detection and Prevention System (IDS / IPS).
Backups
We perform three backups a day of all your data. Each of them is saved on different servers from different providers, for optimal data safety.
ISO 27001 certified
Wideum is ISO 27001 certified. Our information security is achieved by implementing an appropriate set of controls, such as policies, practices, procedures, organizational structures and software functions.

Subsidized by CDTI